A satellite project of labs.iximiuz.com - an indie learning platform to master Linux, Containers, and Kubernetes the hands-on way 🚀
Ivan on the Server Side
|
Hello there 👋 It's Ivan, and it's the end of the month, so you guessed it right - it's time for the traditional monthly roundup of all things Linux, Containers, Kubernetes, and Server Side! The main topic of this issue is... iximiuz Labs for Creators, a shiny new capability I shipped just a couple of days ago. What I was working onMany people have asked me about the possibility of publishing tutorials, challenges, or even courses on iximiuz Labs. While I wasn't against this idea (and technically it was available from day one - some folks even succeeded at it - 1, 2, 3), until very recently, I was a little hesitant to give it a full go. There is a huge difference between a PoC and a product, even when the latter is an MVP (sorry for the slang), and the amount of work needed to package the content-authoring capabilities of iximiuz Labs into a fully-fledged product someone else could use was truly off-putting. Just look at this 5,000-word tutorial I had to write to explain how to write tutorials on iximiuz Labs (yep, recursion). And it's just the tip of the iceberg 😉 But ignoring the demand any further has become impossible lately. Plus, having a handy way to publish learning materials on iximiuz Labs is a mandatory stepping stone for another platform's capability I'm planning to release soon - iximiuz Labs for Trainers (though this is a topic for another newsletter). So, who is the current capability for?
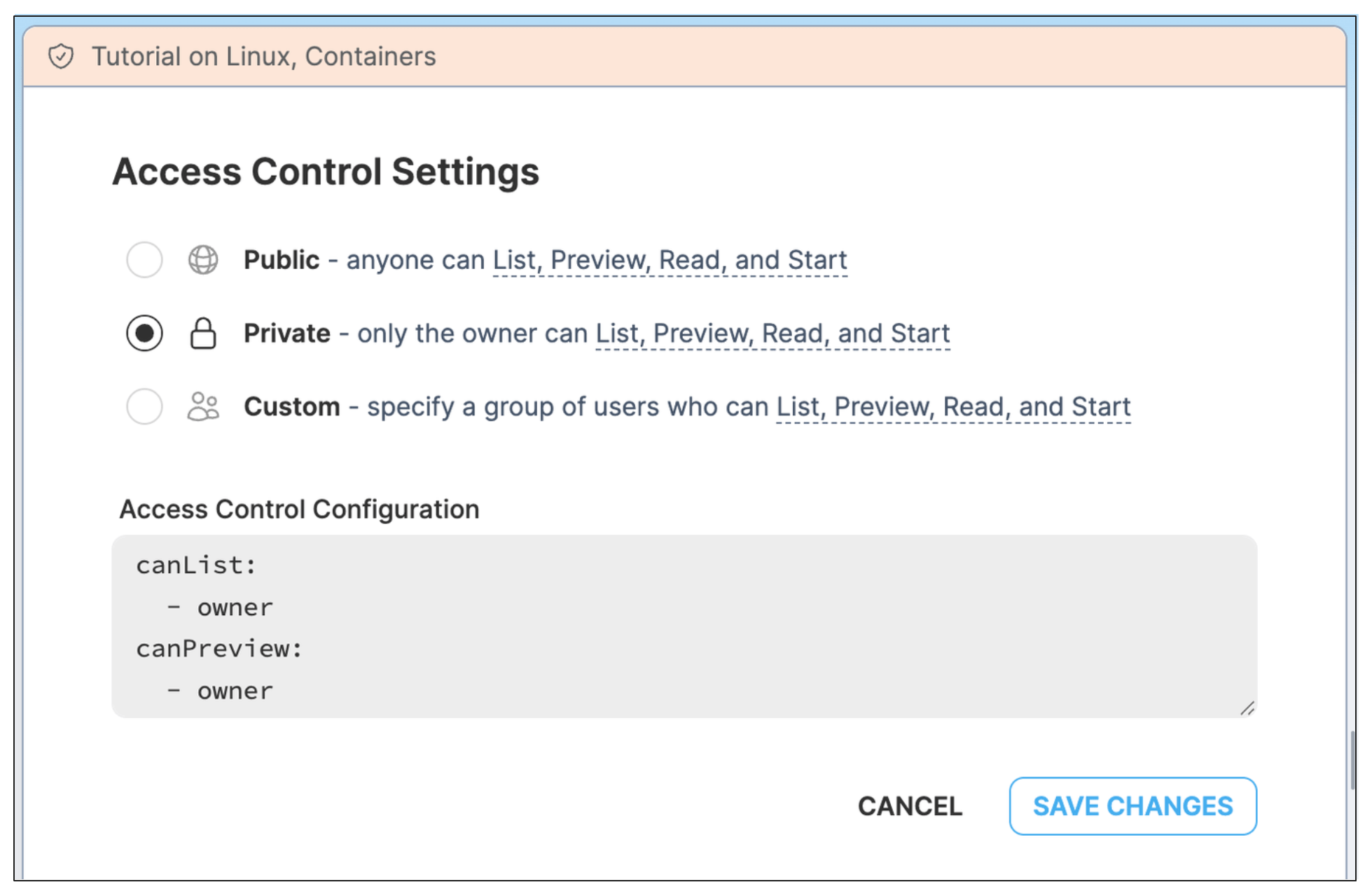
These are the types of potential users I identified, but there will likely be a few more less obvious ones, as it always happens when the rubber hits the road. Ok, enough marketing talk - let's move on to the technical details. Here is what I shipped in March to make the new product happen: Reworked Content CatalogsThe sidebar filter in every site content catalog was extended with a switch between the official, community, and your posts. Content Creation WizardEvery "My Content" section has gotten a "Create Tutorial/Challenge/etc." button, which opens a (hopefully) intuitive wizard. Self-Service Content Access ControlFrom now on, content authors can share their content publicly (or with a limited group of users) in full self-service using a handy UI. Before that, it was a manual process that required me to push the "publish" button (more like to execute a DB update query, but we won't tell anyone 🙈).
Every author can share their content on social media, in their newsletter, or wherever they like with a direct link (e.g., https://labs.iximiuz.com/tutorials/my-awesome-tutorial). Listing the published content in any of the platform's catalogs (a.k.a. "featuring") is also possible, but it remains a subject of my approval (mainly to ensure a certain level of content quality in the catalogs). Reach out if you want some extra exposure for your posts or challenges (just reply to this email or join our #author-experience channel). Content Authoring DocsYay! Documentation!
Since I used iximiuz Labs to publish the docs Markdown Support for PlaygroundsCustom playgrounds are also a form of content, so they deserve the same expressive powers as tutorials, skill paths, or challenges. It's been possible to create your own playgrounds for a few months now, and I can see more than 100 of them in the DB. I chose a few of the most generic (and polished) ones for the recently added community catalog, and I also used my own Getting Started with Istio Playground to showcase the new markdown-powered description and the ability to upload static files (good fit for visuals but you can also use it to ship larger init scripts or even binaries with a custom playground). Exposing HTTPS Services Running in PlaygroundsExposing HTTP services running in playgrounds (a.k.a. "Expose Port" feature) has been available (almost) since day one, but this month, I finally added the ability to expose HTTPS targets. I also fully reworked the "Expose Port" dialog:
The CLI experience is also on par now - the recently added Start & Complete Buttons for Skill PathsLast but not least, Skill Paths finally became first-class citizens of the platform. It is now possible to start following a skill path, and when all its units are completed, mark it as "done", with the corresponding progress reflected in your dashboard. What I was streamingYay! A new category (let's see if it becomes a regular one). After a short break, Kyle Quest and I recorded another episode of our Good Dockerfiles show. This time, we talked about the most typical Python application containerization gotchas. The recording is rather long, but it's packed with practical advice and concrete examples of before and after Dockerfiles. Our experience shows that you are one Dockerfile rewrite away from an 80% vulnerability and 30-50% size reduction. So it's not all doom and gloom! What I was readingIngress-nginx CVE-2025-1974: What You Need to Know - Kubernetes Blog and a deep dive by Wiz - Yet another (quite good) reason not to use Kubernetes if you have other (simpler) options. When a vulnerability shows up in AWS Lambda, App Runner, or any other managed runtime, the mitigation rarely requires your involvement. But with Kubernetes, even if it’s a managed one (e.g., EKS), in many cases, the detection and mitigation will be on your shoulders. Plus, because of its “composite” architecture, it’s more likely to run into a CVE impacting Kubernetes than, say, containerd or Podman - simply because there are (much) more moving parts in a Kubernetes cluster. That’s why I always recommend carefully assessing the requirements, the maximum tolerable complexity, and the available resources to operate the system before choosing Kubernetes over a fully managed service or a simpler deployment option like Podman, Docker, or Kamal. Kubernetes Security Fundamentals series (1, 2, 3, 4, 5, 6) by Rory McCune - Two years ago, I was already sharing Rory’s other great series on container security fundamentals. Time flies! The Kubernetes series covers types (managed and unmanaged) and security-related specifics of Kubernetes distributions, main Kubernetes components (because it’s important to understand what exactly is being secured), authentication and authorization, admission control, and approaches to securing Kubernetes networking in general. containerd socket exploitation: part 1, part 2, and part 3 - If you skip the “exploitation” aspect (which is IMO not the main focus of these posts despite the titles), this series of articles is a great practical example of how to use containerd from the command line (via How do COWs (Containers on Windows) work? - A rare post on Windows-native containers. Not to be confused with Linux containers running on Windows (or macOS) in a hidden Linux VM (managed by a desktop container environment like Docker/Rancher Desktop or Lima). The post walks you through actual Windows subsystems for containers such as Host Compute Service (HCS) and HCSSHIM. An insightful intro for someone looking to become more well-rounded in OS-level virtualization. Life Altering Postgresql Patterns - Postgres has been my primary “production” DB since circa 2014, and I second most of the author’s takes - do use UUIDs for primary keys (and probably prefer v7 over v4 when PostgreSQL 18 is out - it’s time-sortable), add Wrapping upThe main focus this month was on the "feature work". But features for content authors in March should mean a lot of great content in April 😉 I'm keeping my fingers crossed that the iximiuz Labs for Creators product will be well-accepted by its intended audience. And I myself am eager to return to the Docker Hands-On Roadmap. But first, I'll need to wrap up my work on the functionality for trainers, so stay tuned! 🚀 The great news is that iximiuz Labs is becoming much more sustainable to run. This month, the platform's revenue set another record - combined with Patreon sponsorship, it crossed the $7K MRR mark, which is truly astounding and reassuring. Thank you for your support, and happy hacking! Cheers Ivan |
Ivan on the Server Side
A satellite project of labs.iximiuz.com - an indie learning platform to master Linux, Containers, and Kubernetes the hands-on way 🚀